How to Set Up a Proxy for Tor Browser: A detailed guide
In today’s digital age, privacy and security are paramount. The Tor Browser is renowned for its ability to anonymize your web traffic and protect your online identity. However, you can enhance its capabilities even further by configuring a proxy server. This article provides a comprehensive guide on setting up a proxy for Tor Browser, detailing the steps, advantages, uses, and tips on choosing the right proxy server.

How to Set Up a Proxy in Tor Browser
Ensure you have a proxy server before setting up. If you do not own one, you can use Proxy5.net services. They provide high-quality proxy servers that are straightforward to set up and ideal for use with the Tor Browser.
Setting up a proxy in Tor Browser is straightforward, but it requires careful attention to detail. Follow these steps to configure a proxy server for Tor Browser:
Step 1: Download and Install Tor Browser
First, if you haven’t already, download the Tor Browser from the official Tor Project website. Install the browser by following the on-screen instructions.
Step 2: Open Tor Browser and Access Network Settings
Launch the Tor Browser. In the upper-right corner, click on the three horizontal lines to open the menu. Select Options (or Preferences on macOS).
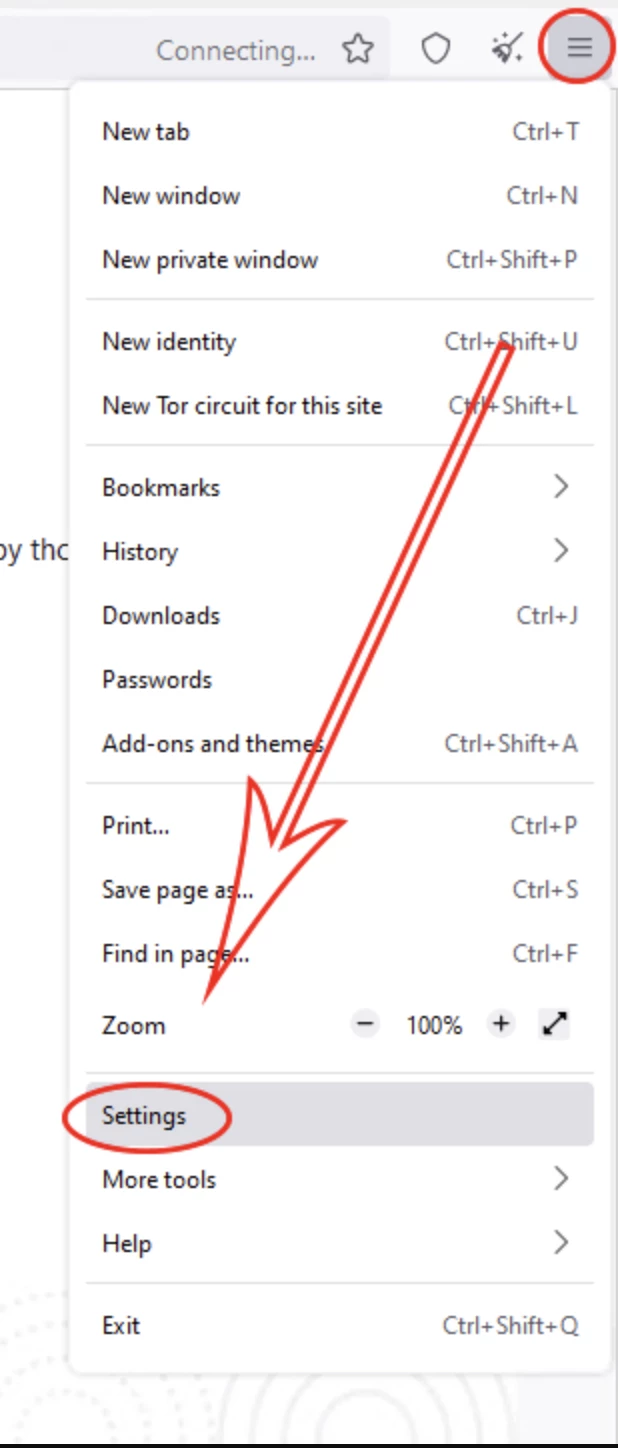
Step 3: Navigate to the Proxy Settings
Scroll down to the Network Settings section. Click on Settings to open the Connection Settings window.
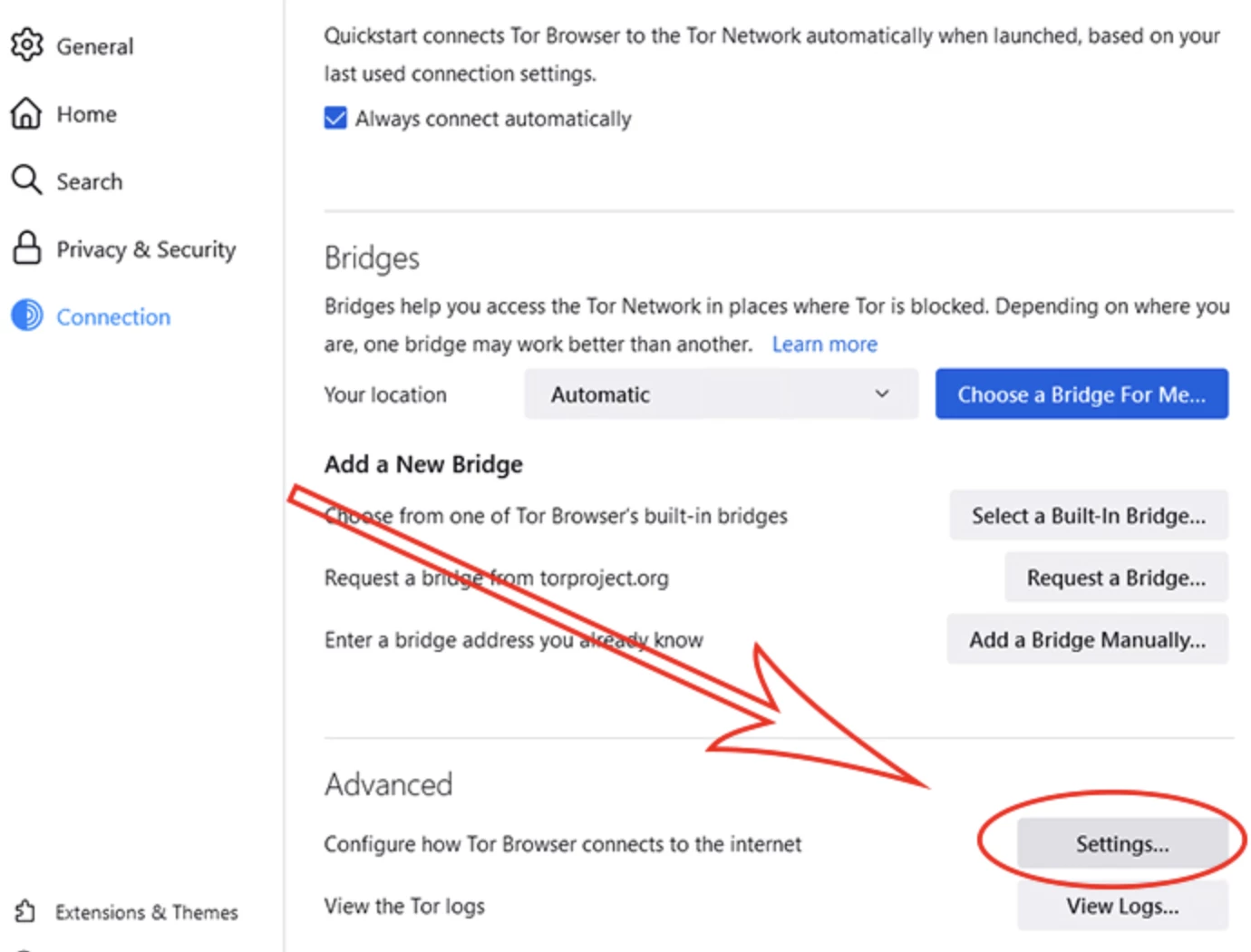
Step 4: Configure the Proxy
In the Connection Settings window, you’ll see several options. Select Manual proxy configuration. Enter the proxy server details, including the IP address and port number. Depending on your proxy type, you’ll need to configure the following:
- HTTP Proxy: For standard web traffic.
- SOCKS Host: For all traffic through the proxy.
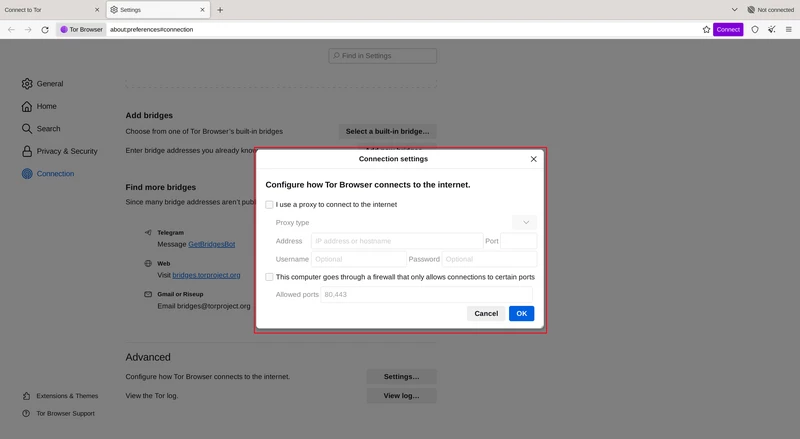
Ensure that you check the Use this proxy server for all protocols box if you want to route all traffic through the proxy.
Step 5: Authentication (If Required)
If your proxy server requires authentication, enter the username and password in the provided fields.
Step 6: Save and Apply
Click OK to save your settings. Restart the Tor Browser to apply the changes.
Step 7: Verify the Proxy Configuration
To make sure your proxy server settings are correct, visit any site that checks your IP address. They should display the IP address of the proxy server, not your real IP.
Advantages of Using a Proxy in Tor Browser
Configuring a proxy server in Tor Browser offers several benefits. Here are some of the key advantages:
- Enhanced Anonymity. A proxy server can add an extra layer of anonymity, making it more challenging for third parties to track your online activities.
- Access to Geo-Restricted Content. Proxies can help you bypass geographical restrictions, allowing you to access content that might be blocked in your region.
- Improved Security. Using a proxy can enhance your security by hiding your IP address and encrypting your traffic, reducing the risk of cyberattacks.
- Bandwidth Savings. Some proxies can compress data, leading to bandwidth savings and faster load times for web pages.
- Avoiding Censorship. In regions where internet access is heavily censored, proxies can help you bypass these restrictions and access the open web.
- Load Balancing. Proxies can distribute traffic across multiple servers, balancing the load and reducing the risk of server overload.
- Filtering Content. Proxies can filter out unwanted content, such as ads and malicious websites, providing a cleaner and safer browsing experience.
In summary, using a proxy with Tor Browser significantly enhances your privacy, security, and access to restricted content.
How Users Utilize Proxies for Tor Browser
Proxies are versatile tools that can be used in various ways with Tor Browser. Here are some common applications:
- Anonymous Browsing. Users often configure proxies to maintain anonymity while browsing the internet, ensuring their activities remain private.
- Accessing Blocked Websites. Proxies enable users to access websites that are blocked by their internet service provider or government.
- Bypassing Geo-Restrictions. By using proxies located in different countries, users can access geo-restricted content such as streaming services and news websites.
- Secure Online Transactions. Proxies provide an additional layer of security for online transactions, protecting sensitive information from cybercriminals.
- Research and Data Collection. Researchers and data analysts use proxies to collect data from multiple sources without revealing their IP address.
- Testing and Development. Developers use proxies to test websites and applications from different locations, ensuring they function correctly worldwide.
- SEO and Marketing. SEO professionals and marketers use proxies to monitor search engine rankings and gather competitive intelligence without being flagged for multiple requests from a single IP.
- Social Media Management. Social media managers use proxies to manage multiple accounts and automate posting without risking account bans.
- Online Gaming. Gamers use proxies to reduce latency and access gaming servers in different regions.
- Avoiding Bandwidth Throttling. Proxies help users avoid bandwidth throttling imposed by their internet service providers, ensuring a smoother online experience.
The versatility of proxies makes them valuable tools for a wide range of applications, from personal privacy to professional tasks.
Choosing the Best Proxy Server: Paid vs. Free
When selecting a proxy server for Tor Browser, you have two main options: paid and free proxies. Each has its own set of advantages and disadvantages.
Paid Proxies
Advantages:
- Reliability: Paid proxies typically offer more reliable connections with less downtime.
- Speed: They often provide faster connection speeds, which is crucial for streaming and downloading.
- Support: Paid services usually come with customer support, helping you resolve any issues quickly.
- Security: Paid proxies offer better security features, including encryption and malware protection.
Disadvantages:
- Cost: The primary downside is the cost, as you’ll need to pay a subscription fee.
- Setup Complexity: Some paid proxies require more complex setup processes.
Free Proxies
Advantages:
- Cost-Free: The most significant advantage is that they are free, making them accessible to everyone.
- Ease of Use: Free proxies are generally easy to set up and use.
Disadvantages:
- Unreliability: Free proxies are often less reliable, with frequent downtimes and slower speeds.
- Limited Features: They typically lack advanced features and support.
- Security Risks: Free proxies may not offer the same level of security, making them more vulnerable to attacks and data breaches.
What to Look for in a Proxy Server
When choosing a proxy server for Tor Browser, consider the following factors:
- Speed: Ensure the proxy offers sufficient speed for your needs.
- Security: Look for proxies with robust security features to protect your data.
- Reliability: Choose a service known for its uptime and reliability.
- Customer Support: If opting for a paid proxy, check the quality of customer support.
- Geographical Coverage: Ensure the proxy offers servers in locations that are beneficial for your use case.
- Compatibility: Verify that the proxy is compatible with Tor Browser.
While both paid and free proxies have their merits, paid proxies generally offer better performance, security, and support. Consider your needs and budget when making a decision.
Setting up a proxy for Tor Browser is a powerful way to enhance your online privacy, security, and access to restricted content. By following the steps outlined in this guide, you can configure a proxy server to work seamlessly with Tor Browser. Whether you choose a paid or free proxy, the key is to select one that meets your needs and provides reliable, secure connections. With the right proxy setup, you can enjoy a safer and more versatile browsing experience.






